Thanks Negan. I just searched for those 2 aren't offered in any of my channels.
Posts by VictorM
-
-
Just watched this yesterday: Kubo and the Two Strings ( Plex channel )
External Content youtu.beContent embedded from external sources will not be displayed without your consent.Through the activation of external content, you agree that personal data may be transferred to third party platforms. We have provided more information on this in our privacy policy.Good tale
-
 Dissecting YouTube’s Malware Distribution Network - Check Point ResearchResearch by: Antonis Terefos (@Tera0017) Key Points Introduction In recent years, threat actors have continuously adapted their tactics to discover new and…research.checkpoint.com
Dissecting YouTube’s Malware Distribution Network - Check Point ResearchResearch by: Antonis Terefos (@Tera0017) Key Points Introduction In recent years, threat actors have continuously adapted their tactics to discover new and…research.checkpoint.comThe YouTube Ghost Network is a collection of malicious accounts operating on YouTube. These accounts take advantage of various platform features, such as videos, descriptions, posts (a lesser-known YouTube feature similar to Facebook post) and comments to promote malicious content and distribute malware, while creating a false sense of trust. The majority of the network consists of compromised YouTube accounts, which, once added, are assigned specific operational roles. This role-based structure enables stealthier distribution, as banned accounts can be rapidly replaced without disrupting the overall operation.
The description of such videos follows a typical “structure”, with a download link and password shared. Step-by-step instructions are often provided, commonly advising users to “temporarily” disable Windows Defender. In most cases, the malware distributed is an infostealer, designed to exfiltrate user information and credentials to a malicious command and control (C2) server.
One video, which has garnered around 10,000 views, advertises cryptocurrency software and instructs viewers to follow a link provided in the description. This link redirects users to a phishing page hosted on sites.google.com, created by the threat actor, which also shares the password for a password-protected archive containing the malicious payload.
During this campaign, the threat actor utilized two different platforms to host the same malicious file, providing redundancy and increasing stealth in case one instance was detected or reported. Another observed tactic is the upload of large files, which are often overlooked by automated scanning systems. Additionally, password-protected archives are used to evade inspection, as security solutions cannot decompress and analyze the contents without the password.
-
Beware of one point though. If you choose to store your passwords locally. And decide to let other PC sync. There will have to be a port opening with a listening process that ought to be classified as a 'server' process. As any good sys admin will tell you, you don't decide a run a server on a whim. Good, restrictive firewall rules have to be made to accompany it. And if on Linux that has apparmor, apparmor profiles have to be made to whitelist allowed exe's and libraries.
-
You might say most hackers are money motivated nowadays, and that there is no value in attacking you. Their target are big companies.
Value is Subjective: While you might not consider your data valuable, hackers might disagree. Even seemingly innocuous information can be exploited. For example:
Personal Information: Names, addresses, phone numbers, and birth dates can be used for identity theft or social engineering attacks. They can be sold.
Login Credentials: Even accounts that seem unimportant could be used to gain access to other accounts or systems. And they can be sold.
Financial Information: Bank account numbers, credit card details, or even utility bills can be used for fraudulent transactions or to open new accounts in his name. Social media accounts can be sold.
Device Access: If hackers gain access to your computer or smartphone, they could use it for malicious activities, like sending spam (still profitable) and launching attacks on other systems. It can also be sold.
The important thing is, while attacking big companies can earn them a lot more money, it is also considerably more difficult to successfully attack. Big companies have the money to buy better defences, the money to employ security teams. While you, the home user, is a much easier target. They might not earn as much per bang, but they can make up for that in numbers. It's is a simple business calculation. If you think it is too troublesome for them to have to attack so many targets, they have hacking tools that make it easy. And they have automation, remember bat files and windows scheduler are automation tools. They don't have to sit there and do it job by job; they just let the task run unattended. Don't be fooled by popular media depiction of a hands on keyboard hacker.
Remember just because you don't see it in security news sites doesn't mean it is not happening. Newspapers don't report petty burglaries either.
Not just money. You actually have no way to predict anyone's motive for doing anything. You are only guessing. Think about that.
You can defend yourself against hackers, you just have to learn how. -
Ubuntu has VPN functionality built in (OpenVPN), all you need to do is download configuration files.
ProtonVPN is based in Switzerland, and is focused on providing free security to all. You can choose the paid option to support them.
Google for "protonvpn free"
Register for the FREE version by supplying your email
You will be given an account with a random secure password
Copy Save that email address and password to text editor in case your browser does not automatically save it, most won't; you can add it back in later.
You can enable 2FA later.
DO NOT download the PROTON VPN CLIENT, scroll down
'OpenVPN configuration files' section
select the 'GNU/Linux' radio button
select either TCP or UDP.; tcp is more reliable, udp is faster
select 'Free Server Configs' radio button
The free account only has 3 countries, Japan, Netherlands and USA, but there are many servers for each
click on several 'Download' buttons to download individual config files for each server
Do not close the browser Tab
-------------------------------------------------------------------------------
Then on Ubuntu,
go to Settings > Network > VPN section: click +
click on Import from File, and select one of the files you downloaded.
A profile will be made for that particular server.
Now it asks for the Username and Password,
log back into your ProtonVPN account.
Go to Accounts on the left.
Go to OpenVPN / IKEv2 username
copy the 'OpenVPN / IKEv2 username' and paste it into the Ubuntu dialog
copy the 'OpenVPN / IKEv2 password' and paste it into the Ubuntu dialog
Click Apply
Now repeat for all the servers configurations you downloaded.
You can now selectively turn on each VPN server in Settings > Network, a vpn icon will show in the top right corner. -
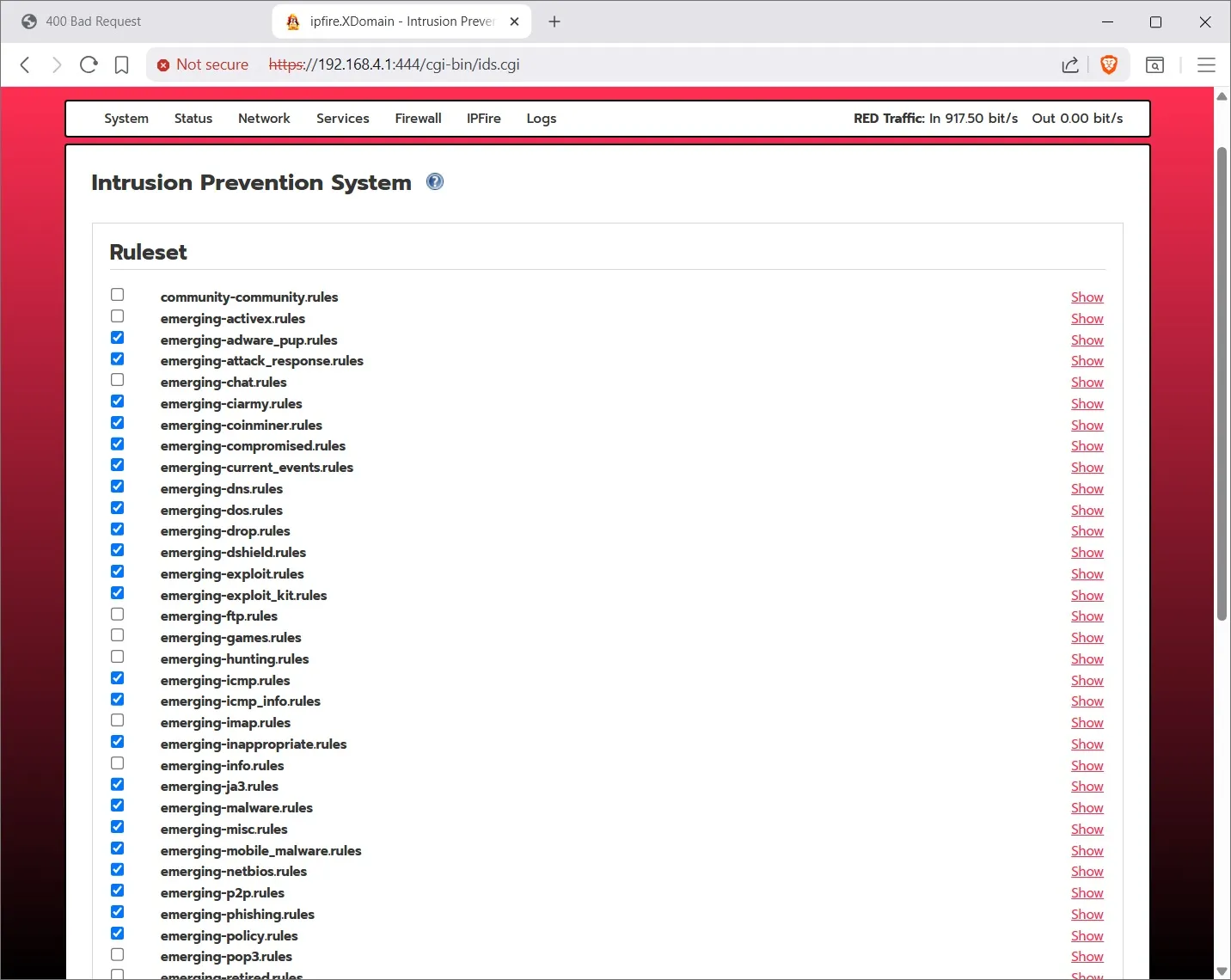
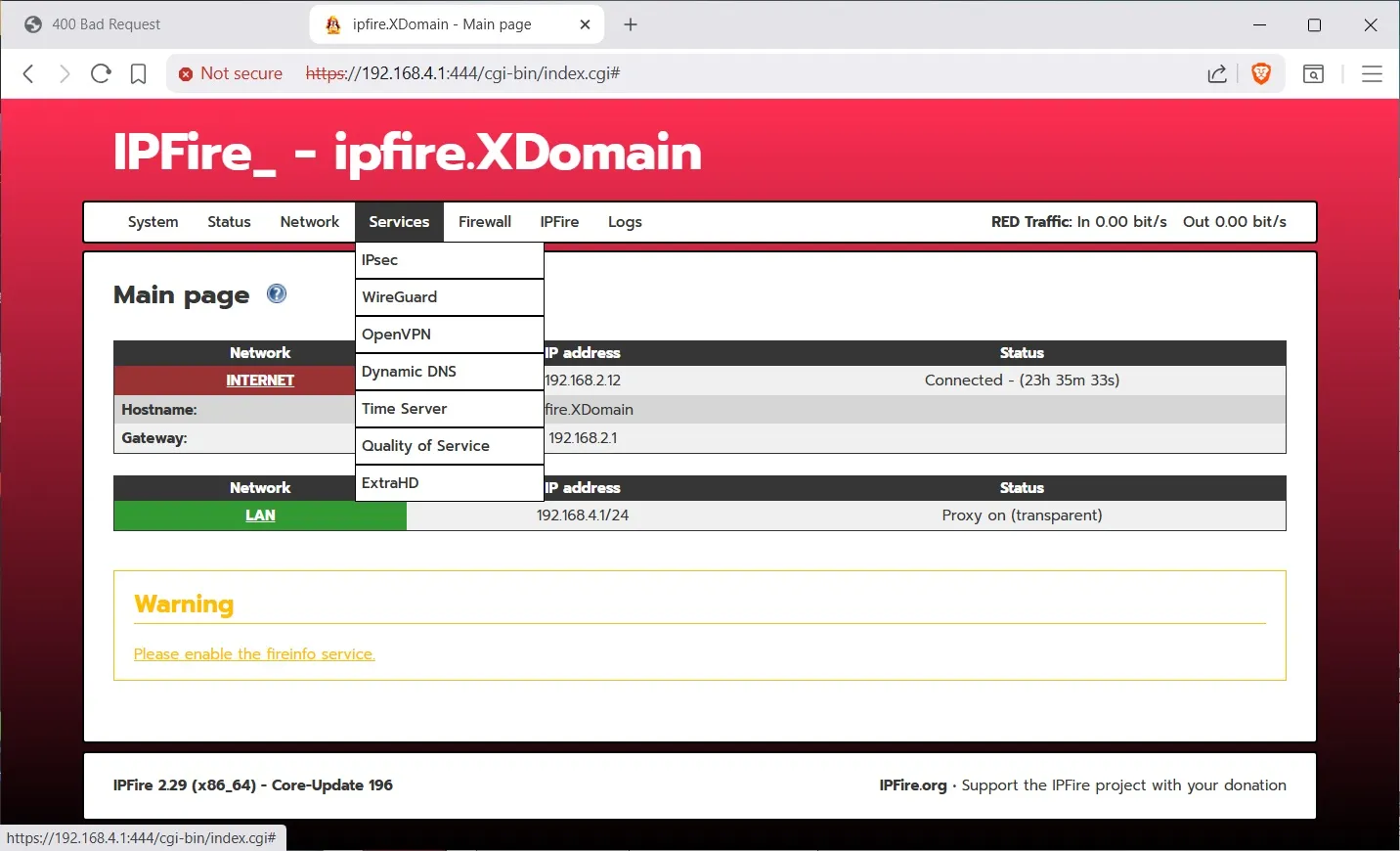
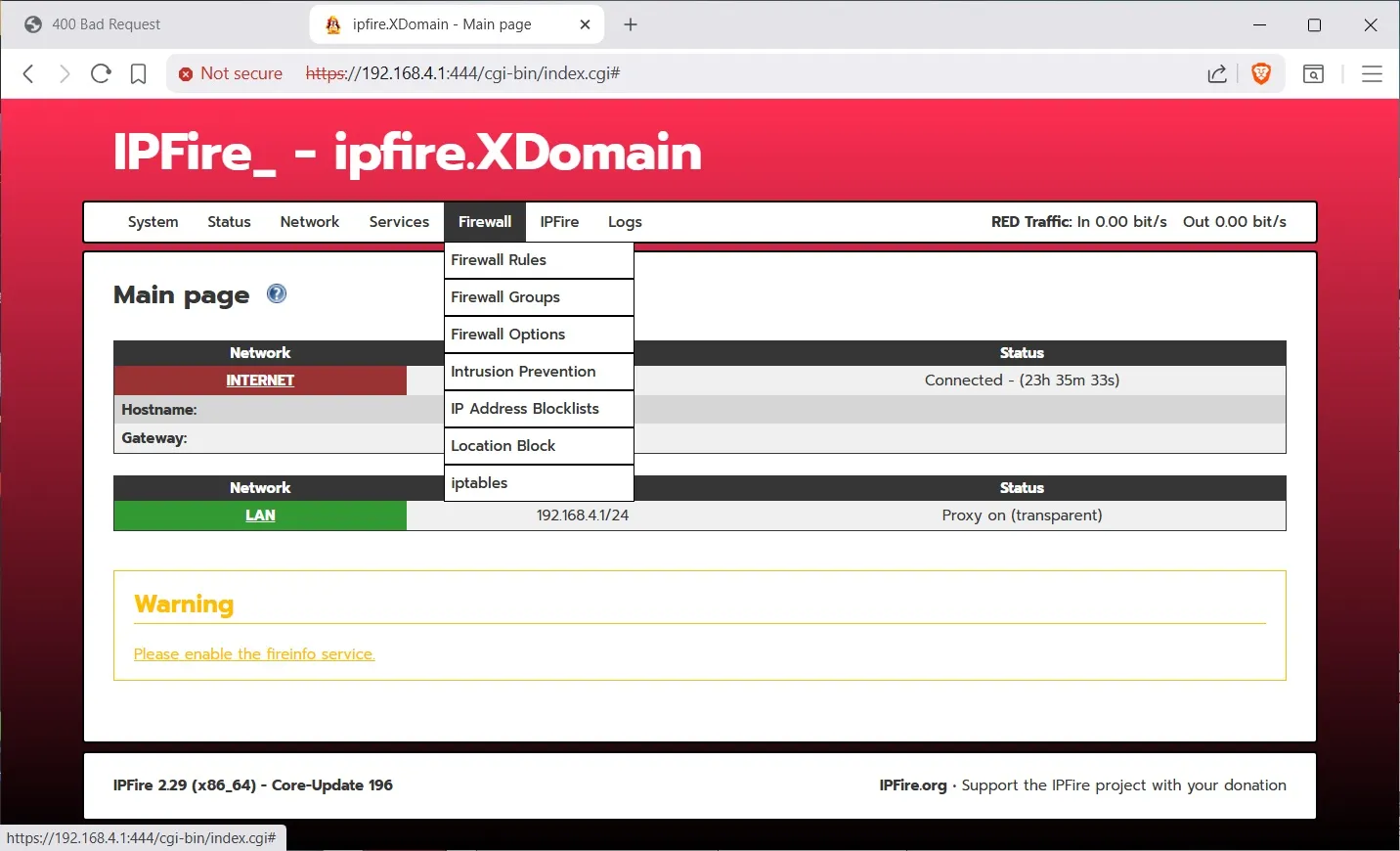
First click on the Add Provider button and add each of the free rules providers. The ones that say Pro Rules and Registered Users are not free.
Now click on Customize Ruleset button and pick the rules that matter to you. For example you won’t be needing ‘emerging activex rules’ since we no longer use Internet Explorer. (IE).
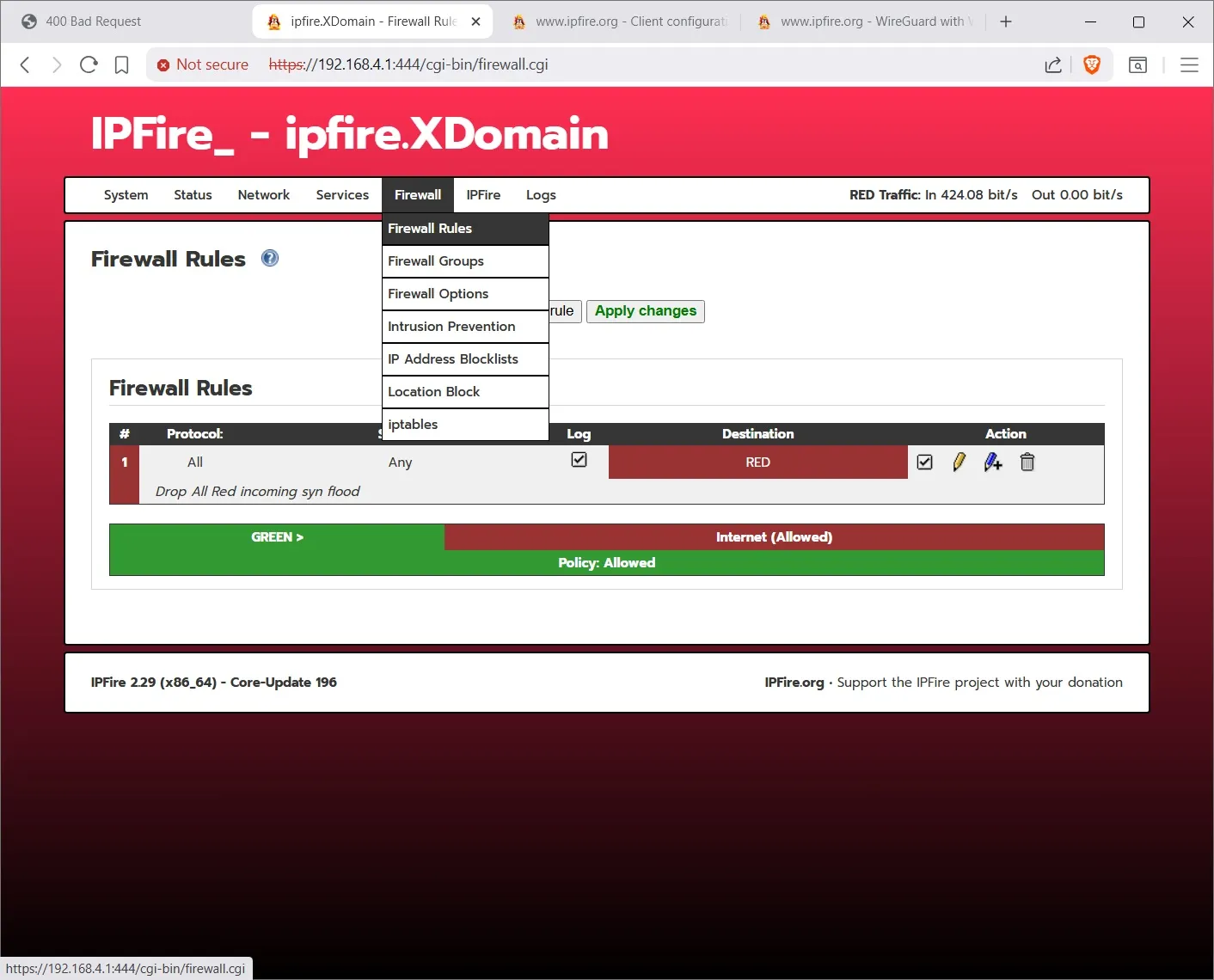
Next, next click on Firewall RulesThe rules defaults to Outbound Allow as policy. That’s why you can surf immediately when you hook up the wires.
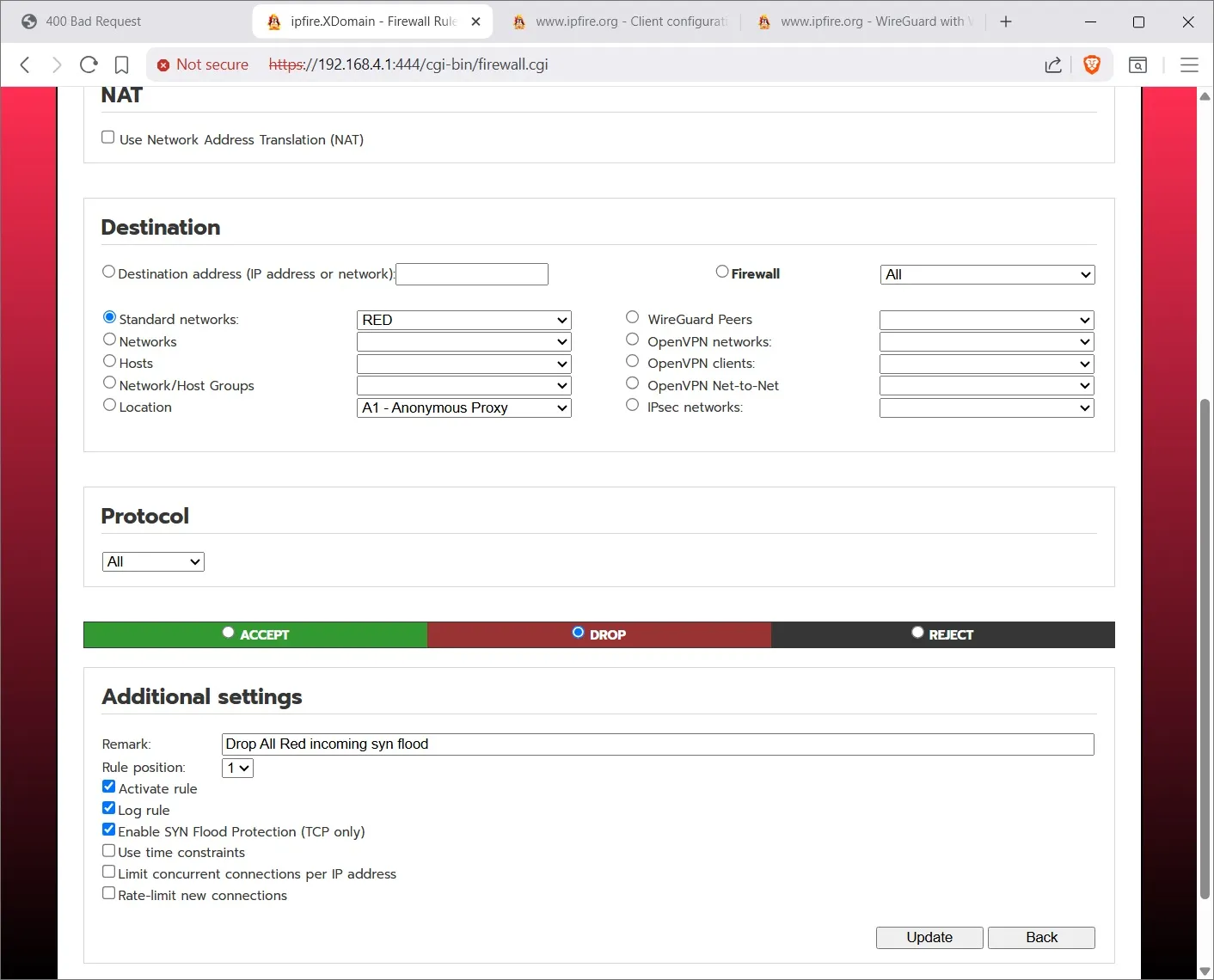
You can trash the Block 25 smtp rule, that’s just for demonstration. I made a rule (using New Rule button) that Drops all incoming on the Red WAN interface and selected the option to Enable SYN flood protection, that is a denial of service attack. The source is ‘standard networks : any’ and the destination is “standard networks : red”. (You can’t see the Source option in the screenshot because I scrolled the screen down.)
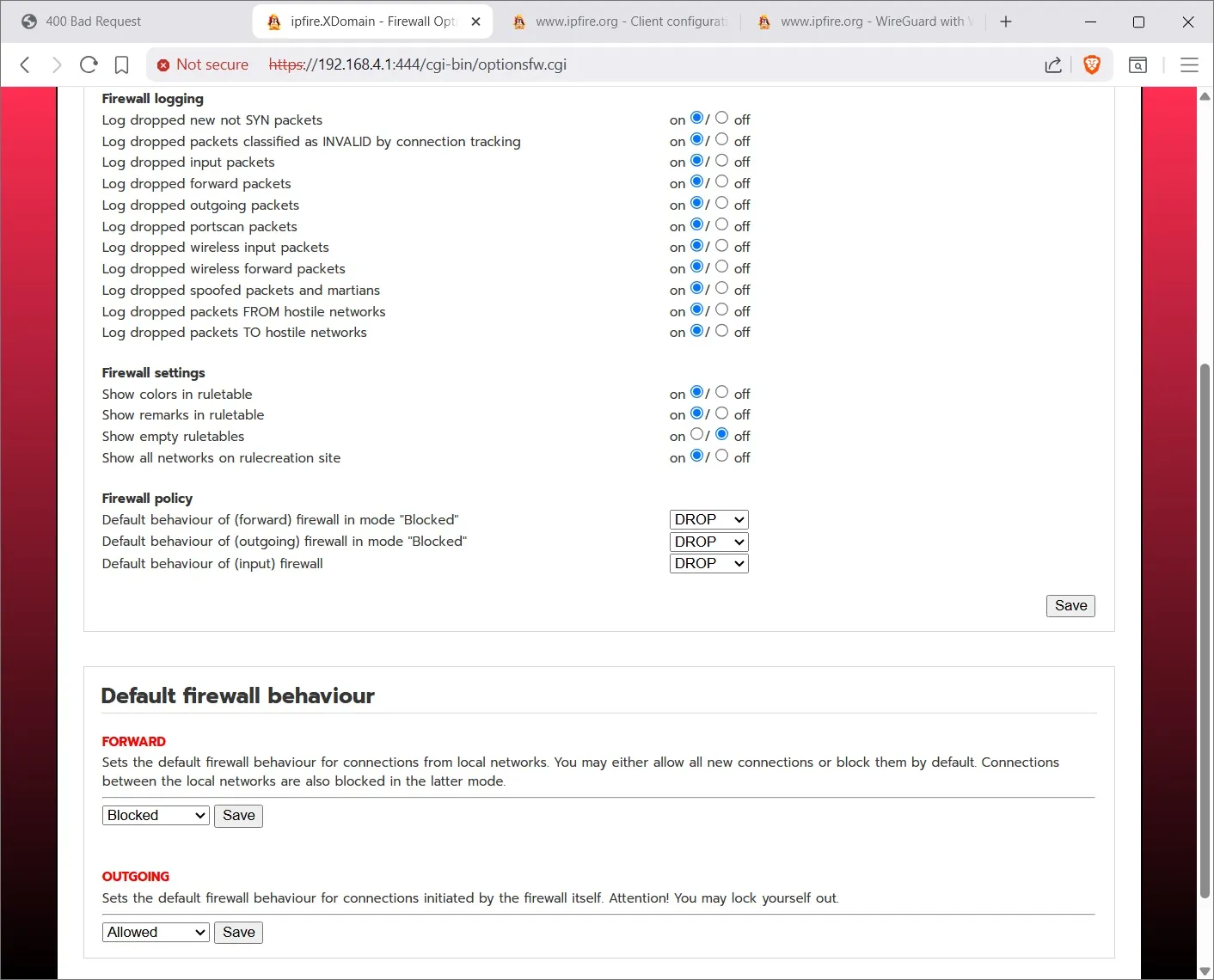
Here I am showing you the Firewall Options. Where the default Outgoing Allow setting is set. Set the Forward to Block, since we are not forwarding any network traffic to somewhere.
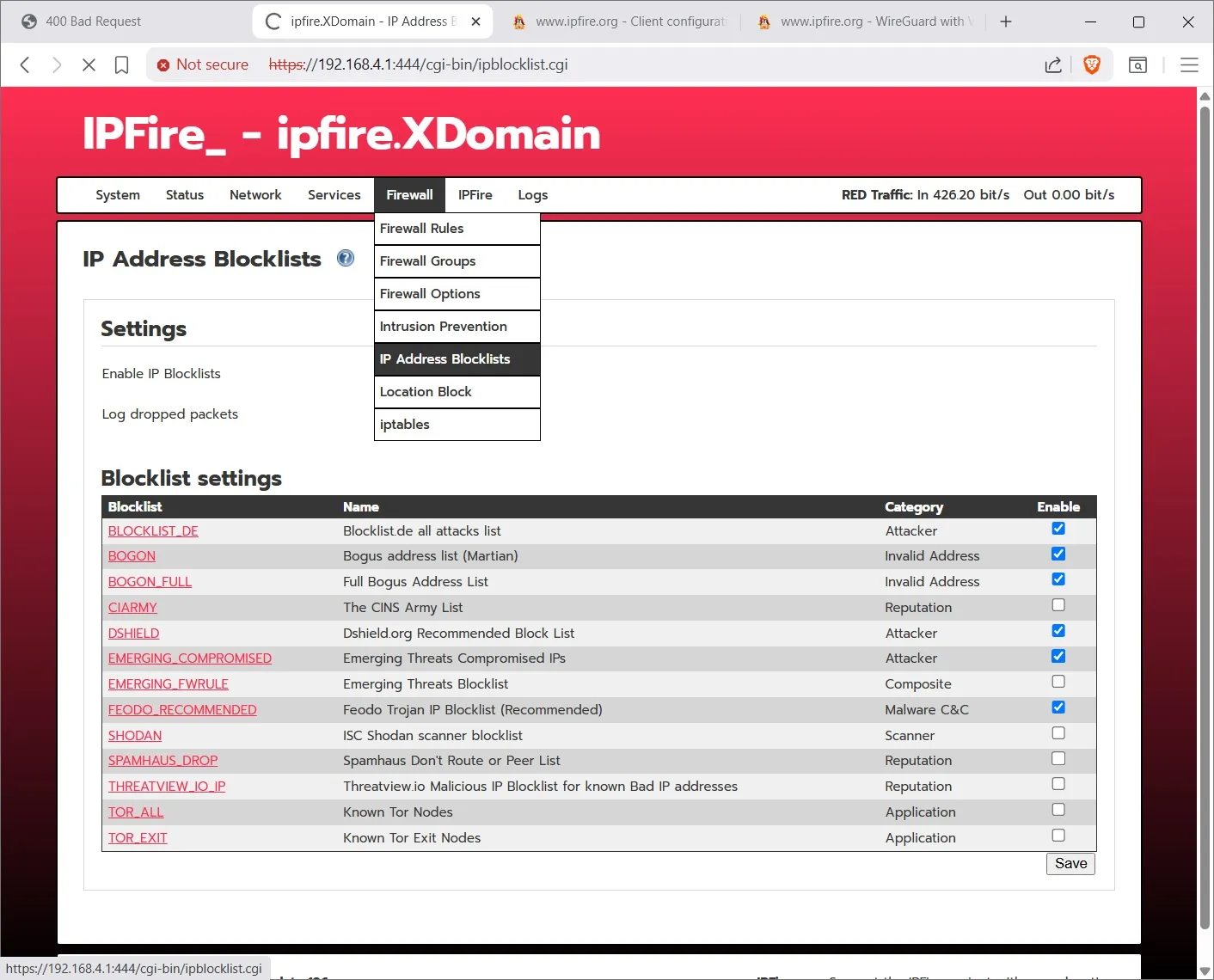
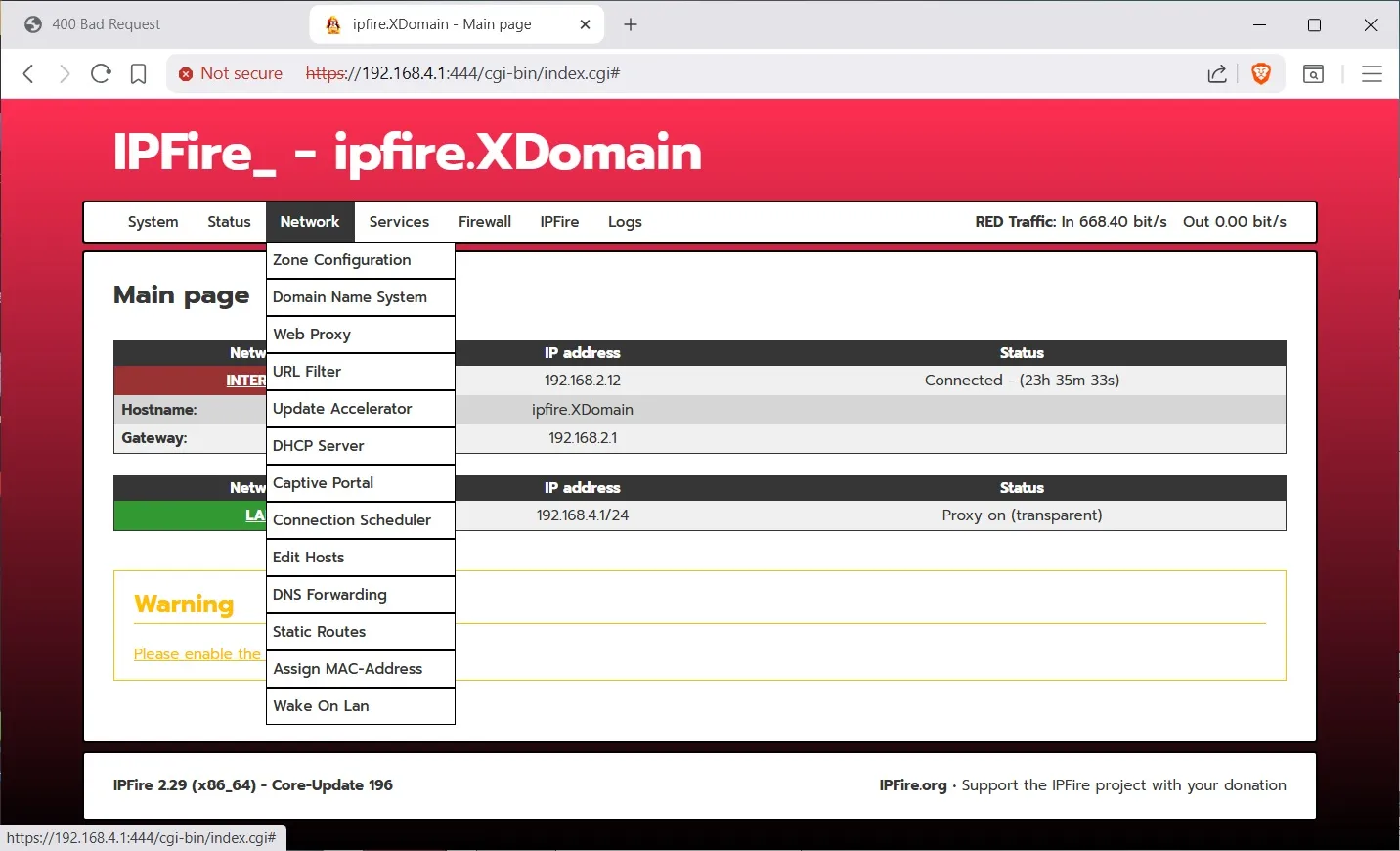
Using IP Address Blocklist you can download various blocklists.
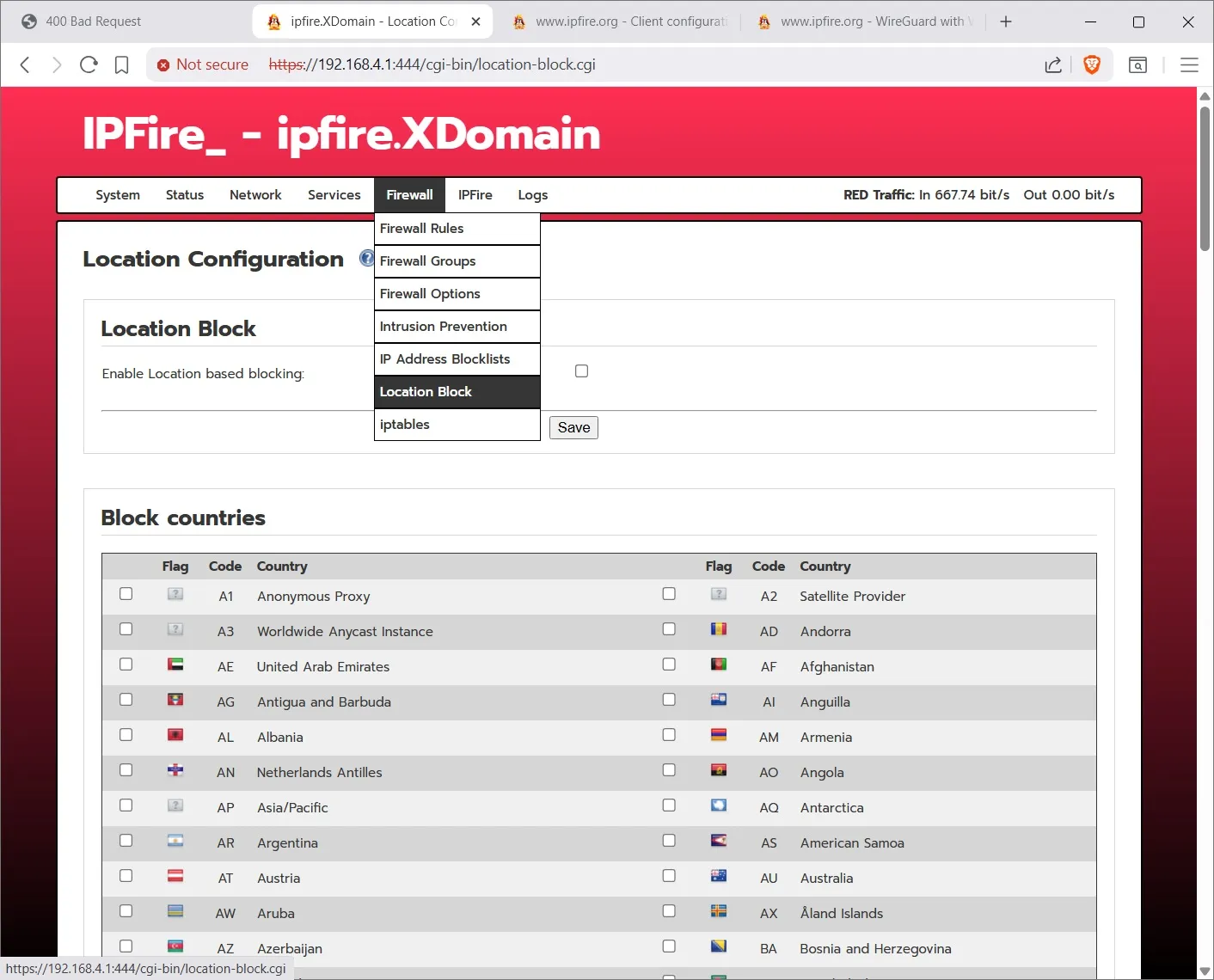
Location Block is where you can block various countries
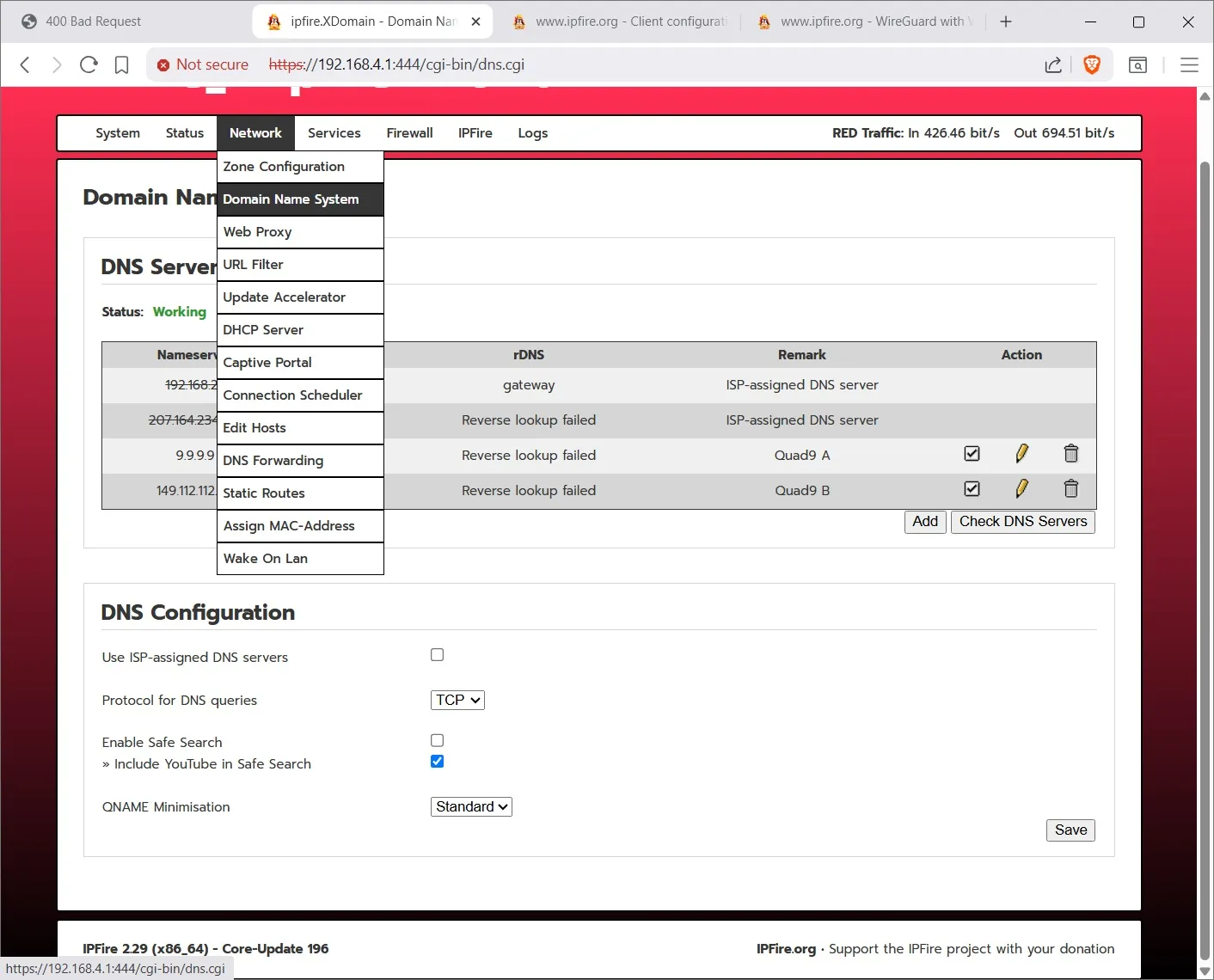
At the DNS screen you can set up your preferred DNS provider. Note you have to wait a little for the entire screen to show up as ipfire tries to verify the addresses as the screen loads.
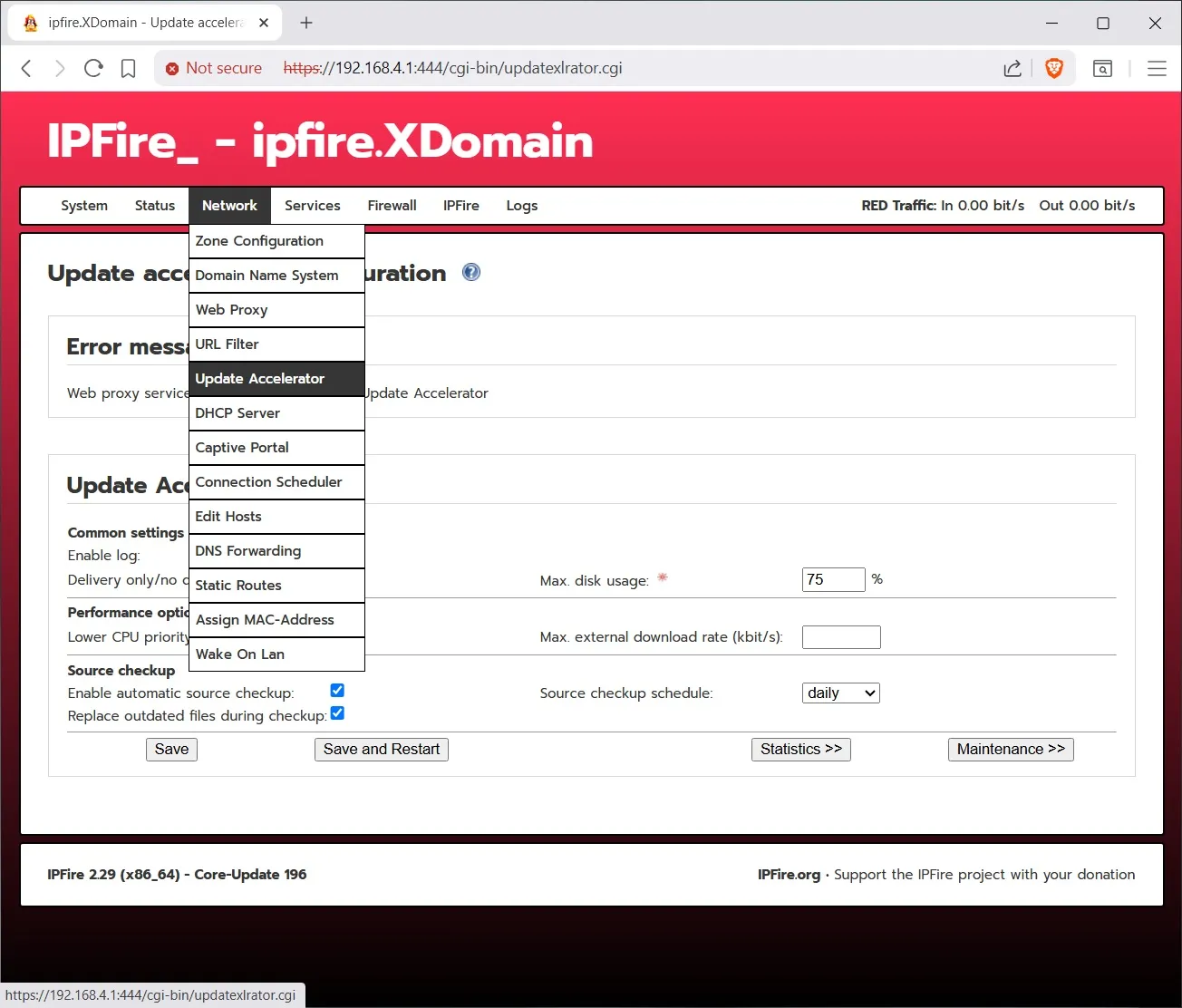
And finally lets look at updates:You checkmark the 2 boxes as above to enable automatic updates.
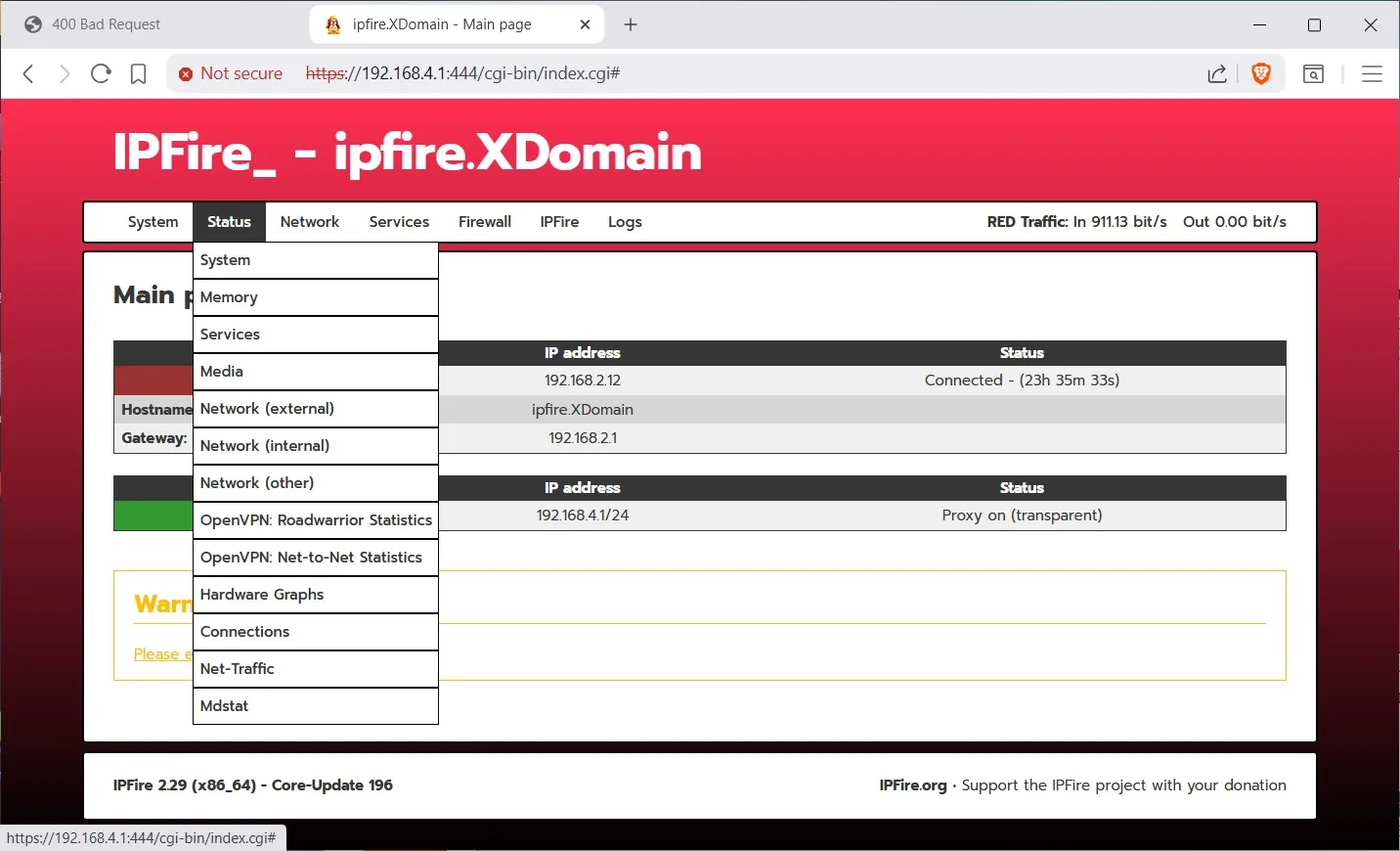
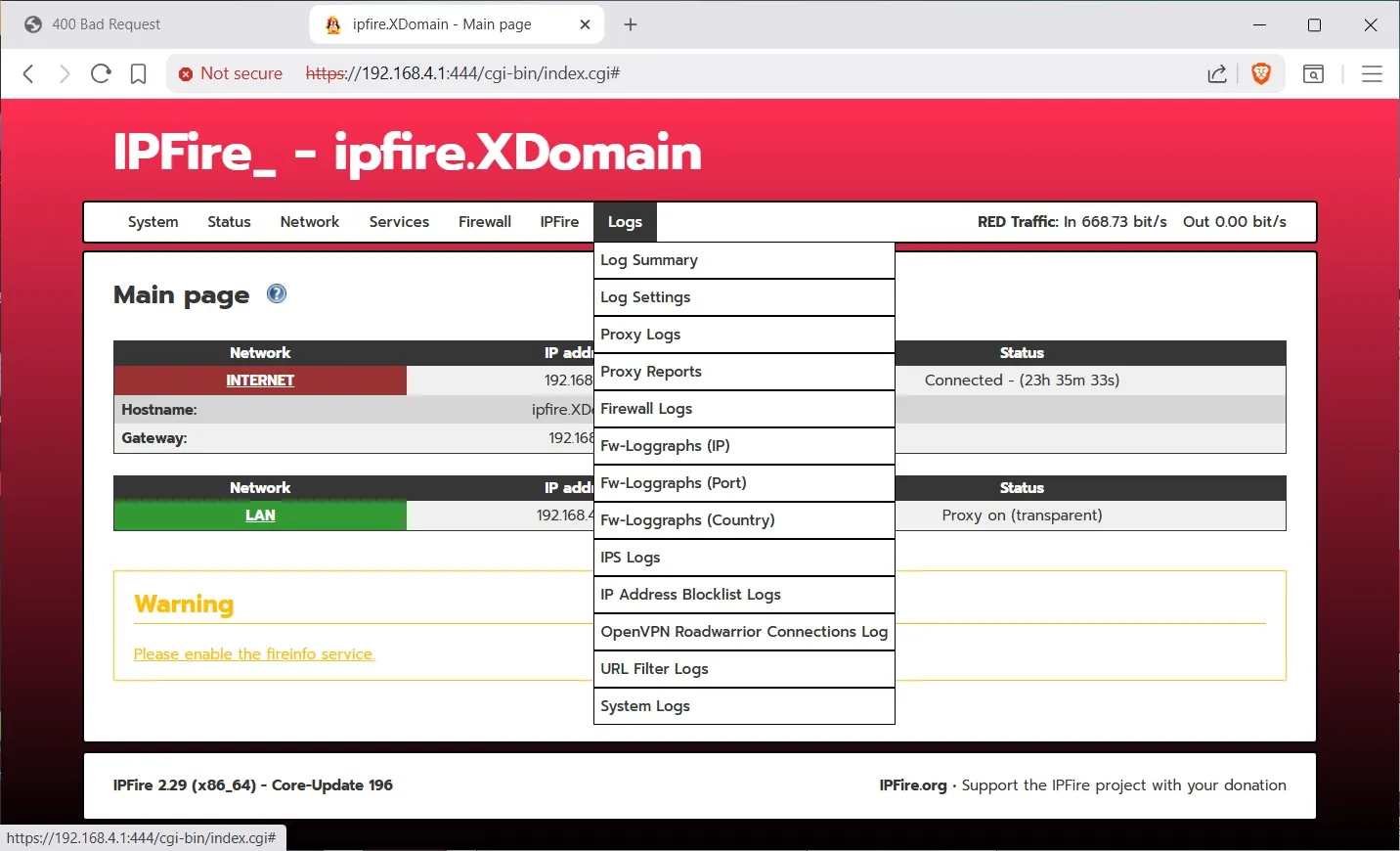
There are other configuration options are you can see on the first few screen shots, but I have chosen the most common screens to configure for us security focused MT users.Note: for the road warriors, you can setup a VPN to connect back to home using the Services>OpenVPN menu. The set up is a little involved, but the instructions are easy to follow. It also supports 2FA. The buttons are not labeled to show you that it is a wizard. See the documentation here: Client configuration
And there are lots of add-ons available thru the ipfire>Pakfire menu. Add-ons -
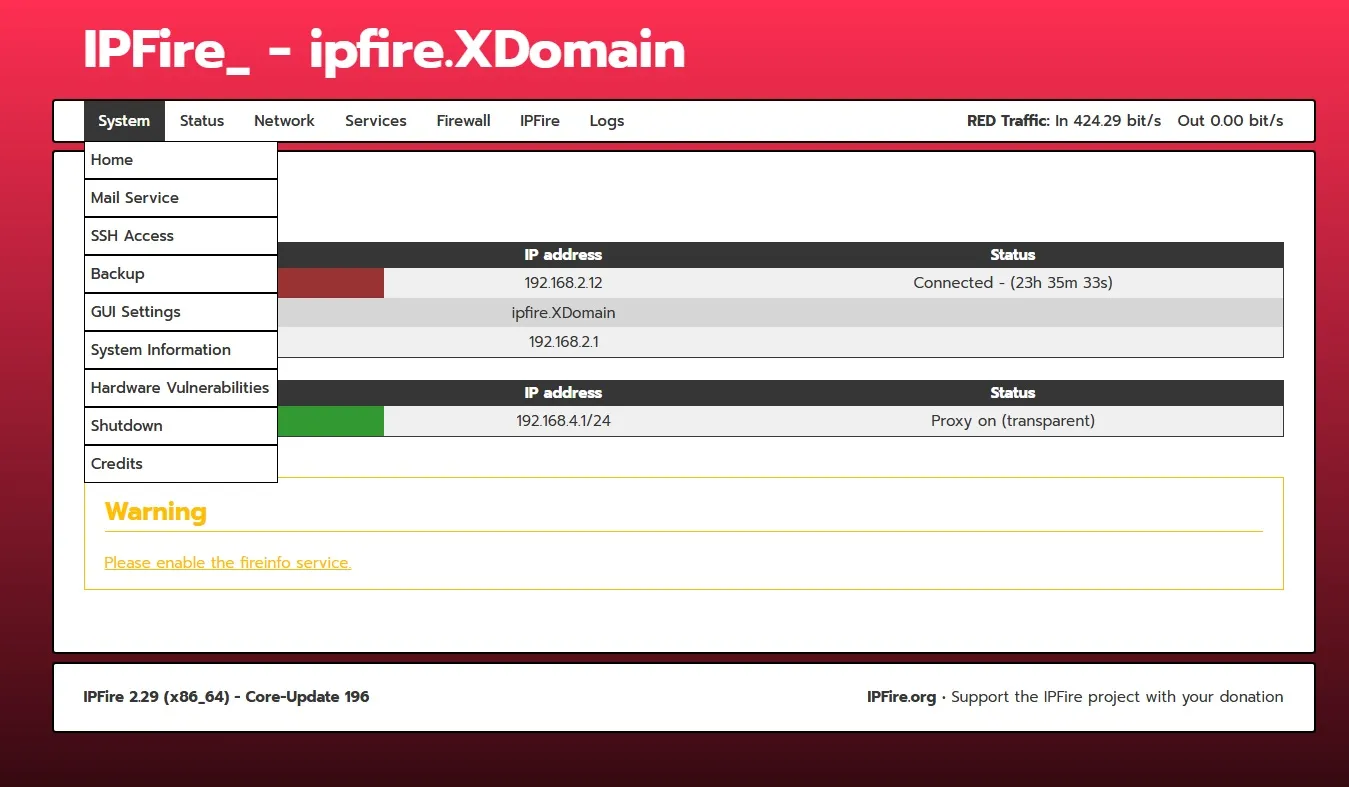
Today I am going to help you setup a ipfire network IPS and firewall.
Having a network hardware fIPS and irewall is good because it can stop attacks centrally at the gate to your LAN. The ipfire machine is your gate.
A network IPS and firewall is essential because your Windows firewall is not as honest as it seems. Numerous sorts of traffic bypasses it without any firewall rules, like base-telemetry, windows update, remote management, push to install, RPC, delivery optimization, pc-sync, and network time service. Where you have unchecked inputs like these, it is very difficult to lock down security. You sometimes do not know whether it is tcp or udp, you do not know the ports and you don’t know what ip addresses are involved because MS does not disclose them. Therefore, a network IPS and firewall that stops traffic at the gate is needed. It can stop network exploits BEFORE it touches your pc's.
Ipfire is very simple to configure. If you have explored your router settings you will find similar sections.
And if you have children, you can set time limits and block unwanted material.
What you need is a old pc, and add a $15 2nd network card and a $12 dumb switch. Then install ipfire on it and it will act as a hardware IPS and firewall. Beats buying a hardware appliance at $2XX.You download the iso and use Rufus to write it to a USB stick, or if your old pc is too old to boot from USB, then you right click and Burn to DVD disc. Machines as old as Core-2-Duo’s with 4GB RAM will suffice as a firewall doesn’t use much cpu power. The suricata IPS just needs RAM ( and 4 gb is plenty, minimum just 1 gb ).
When it boots up, it will ask you to select which network card you want to use for your WAN (red) and LAN (green). Don’t worry if you get it wrong, you can always switch the Ethernet wires. Then it asks for two passwords; one for root which you won’t use much, and the admin; which you use to login to the web panel. And then you decide what ip address to give it.
Then you surf over to xxx.xxx.xxx.xxx:444 . Note the :444, because ipfire does not use https 443.
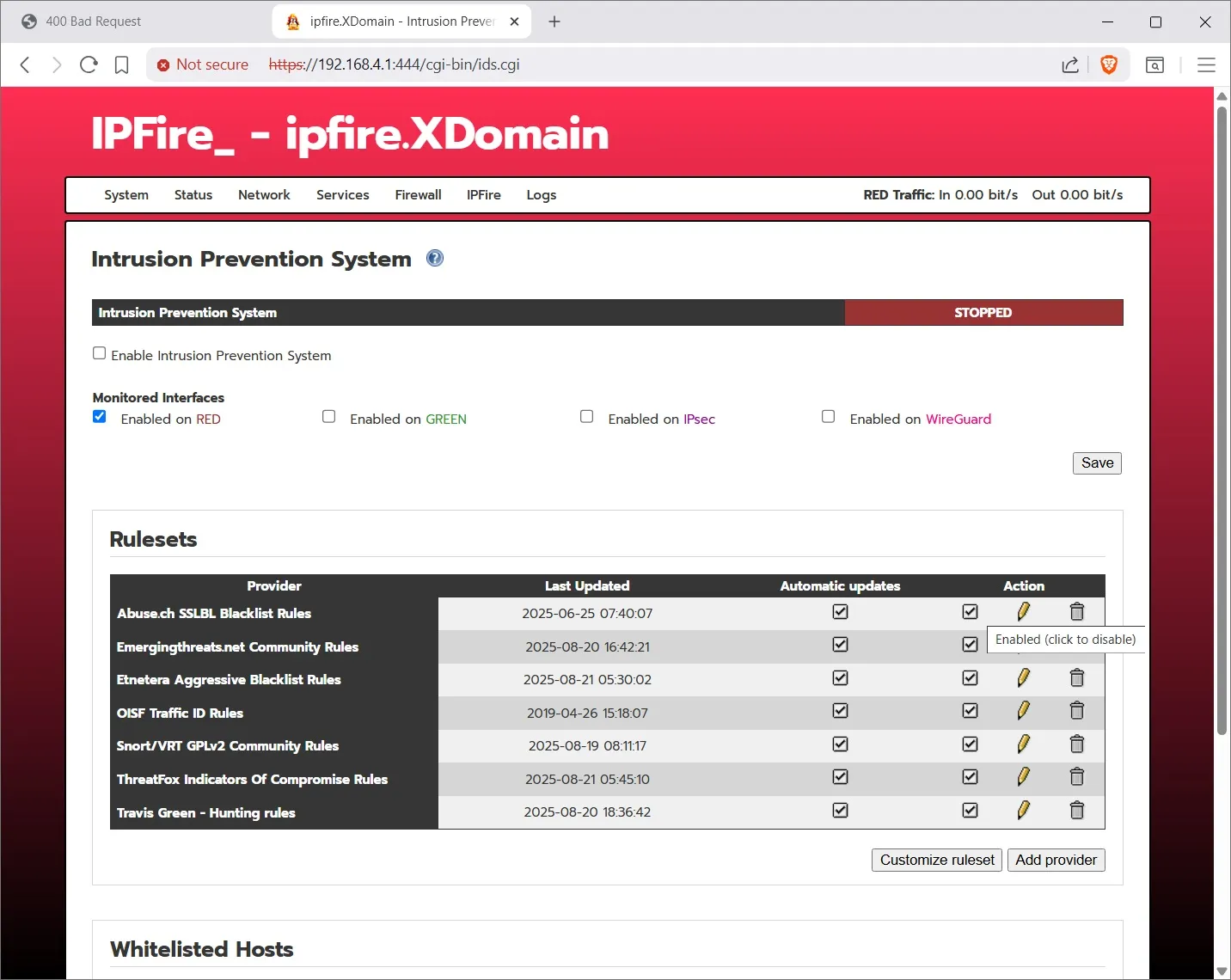
Lets talk about the Intrusion Prevention System. -
Start > All apps > Windows Tools > Windows Defender Firewall
Click on Windows Defender Firewall Properties on the center section.
Click on each profile (Domain, Private, Public) tab- change Outbound connection = Block
- Specify Logging settings for Troubleshooting > Customize
- Size Limit = 100000 KB
- Log Dropped packets = Yes
- Log Successful connections = Yes
HowTo allow a windows service outbound: Click on Outbound Rules on the left, click on 'New Rule', select 'Custom', next to 'Services' click customize, select 'Apply to this service', scroll and find 'Windows Update', next, ports and protocol - (no change), next, IP addresses ( no change ), next, select 'Allow The Connection'. Checkmark all profiles,next. Give the rule a name, eg "Allow service X".
HowTo Allow a program outbound: Click on Outbound Rules on the left, click on 'New Rule', Select "Program", next, select "This program Path" and click on "Browse" button, Navigate to program folder and select the EXE, next, select "Allow the connection", Checkmark all profiles,next. Give the rule a name, eg "Allow Program X".
HowTo Allow communication to a destination port # and IP address: Click on Outbound rules on the left. Click on 'New Rule'. Select 'Custom'. next. Select 'All Programs'. next. For 'Protocol Type' select 'TCP' or 'UDP' as the case may be. For 'Remote Port', select 'Specific Ports'. Then type in the port number(s) below. next. For 'Remote address this rule applies to' select 'These ip addresses'. Click 'Add' button, and in the following dialog box, type in an ip address into 'This ip address or subnet'. ok. next. Select 'Allow the connection'. next. Checkmark all profiles,next. Give the rule a name, eg "Allow out to port ### on server YYY.
HowTo Allow or Block a Package: Click on Outbound rules on the left. Click on 'New Rule'. Select 'Custom'. Keep clicking Next button until you see "Allow the connection" and "Block the connection", select the one you want. Click next until you reach Finish, and name the rule. Then choose the rule just created and select Properties. Go to 'Program and Services' tab. Go to 'Application Packages' settings. Go to 'Apply to this application package' and select the package. OK. OK.- --------New Rules you have to Add--------------------
- Outbound/ allow \windows\system32\svchost.exe
- Outbound/ allow \windows\system32\svchost.exe TCP, Service: Windows Update
- Outbound/ allow \windows\system32\DeviceCensus.exe (related to Windows Update)
- Outbound/ allow \windows\system32\svchost.exe TCP, Service: Windows Time, UDP, remote port 123, remote ip: <your router's ip> (you will also need to modify Control Panel > Date and time > Internet Time)
- Outbound/ allow C:\program files\windows defender\msmpeng.exe
- Outbound/ allow \windows\system32\AuthHost.exe (for MS Account setup, Mail, Calendar)
- Outbound/ allow \windows\system32\smartscreen.exe (so that Windows does a reputation check on downloaded files before running)
- Outbound/ allow \windows\system32\WWAHost.exe (for MS Account sign in)
- Outbound/ allow program <Firefox/Chrome/Opera, whichever browser you use> Remote ports=TCP 80,443
- Outbound/ allow MS Chromium Edge (C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe), Remote ports=TCP 80,443
- Outbound/ allow program \users\<userAccountName>\appdata\local\microsoft\onedrive\onedrive.exe. (if you choose to use OneDrive, each account that uses OneDrive needs a rule )
- Outbound/ allow Core Networking DNS (TCP-HTTPS): TCP, Remote Port 853 and 443, Remote ip: 9.9.9.9,1.1.1.1
- --------Rules you have to Modify-------------------------
- Outbound/ allow Core Networking - Dynamic Host Configuration Protocol (DHCP out), Remote ip: (as found by DHCP Server in ipconfig /all)
- Outbound/ allow Core Networking DNS (UDP-out): UDP, Remote Port 53, Remote ip 9.9.9.9, 1.1.1.1
- --------Existing Rules to leave as is--------------------
- Outbound/ allow Windows Defender SmartScreen (packageMicrosoft.Windows.AppRep.ChxApp_cw5n1h2txyewy")
- Outbound/ allow Core Networking - Dynamic Host Configuration Protocol (Ipv6-DHCP out)
- Outbound/ allow Core Networking - IPv6 (IPv6-Out)
- Outbound/ allow NcsiUwpApp (Network Connectivity Status Indicator Universal Windows Platform App)
- Outbound/ allow Recommended Troubleshooting Client (HTTP/HTTPS Out)
- Outbound/ allow Windows Security (SecHealthUI)
- --------Then you do this---------------------------------
- Outbound/ Disable all other Outbound rules with a Green Dot ( which means they are active ).
--------Rule you have to modify-------------------------- - InBound/ allow Core Networking - Dynamic Host Configuration Protocol (DHCP in), from ip: (as found by ipconfig /all)
- --------Existing Rules to leave as is--------------------
- Inbound/ allow Core Networking - Dynamic Host Configuration Protocol (Ipv6-DHCP in)
- InBound/ allow Windows Security (SecHealthUI)
- --------Then you do this---------------------------------
- InBound/ Disable all other Inbound rules with a Green Dot ( which means they are active )
Note: I use the DNS Servers 9.9.9.9 (Quad9's malware sites blocking DNS) and 1.1.1.1 (CloudFlare's DNS - the fastest) You will need to change your DNS Servers in Network Adapter > IPv4 Properties if you choose to use them.
Side Note: You can disable several rules at once by clicking on the first line, and Shift-clicking on the bottom line, then right-click and choose Disable
Some Win apps (like those downloaded from the Store) install Inbound allow rules to itself. When you install an app, you should check the Inbound rules to see if any new rules have appeared, and disable those if you don't want inbound traffic to that app. Note that an inbound rule to an app essentially makes that application a server. That is, it will accept any transmission to itself all the time, and can be exploited
Together, these firewall rules implement the Default Deny firewall principle. And each firewall rule aims to be very specific: it specifies the ports to use, and it specifies the ip address to use. (except when I don't know, like where the smartscreen servers are, MS does not publicize these things) This is so that they cannot be misused by malware; a overly wide rule will just allow DNS to go outbound. But to where? Malware and hackers will use a default wide rule to use as a back channel to communicate with it's server. I am being slack here, a good firewall administrator will scour the firewall logs to see exactly where the nearby MS servers are and specify them in his/her firewall rules. But the default Outbound Allow All policy is a definite no-no.
However, I should add that an Outbound Default Deny policy requires work to add rules for every program you install that requires access. For people who try out lots of programs for fun, this would induce some, err, hardship. A Default Deny policy is best for those who demand security and don't change their configuration lightly.
Hackers have ways to get around Outbound Deny. One way is to use DLL Injection to an already allowed app. The way around this is to only allow the absolutely necessary things to go outbound, and disable built in Windows features where possible. Here are a few examples. a) You can assign manual ip address in Network Adapter IPv4 Properties. Then the DHCP rule for fetching an ip address for your machine from the router can be disabled. b) IPv6 can be disabled totally. You risk not reaching a web site using that protocol, but chances are slim, because since the creation of NAT routers, many gov and corp internal machines can now use private IPv4 addresses that are not routable on the internet ( 192.168.x.x, 172.16-32.x.x, and 10.x.x.x ). So the IPv6 outbound rule can be disabled. c) MS Edge rule. MS Edge runs automatically and invisibly upon every login. If you use a different browser, then this rule can be disabled. The MS Edge rule was included above only as a backup in case your favorite browser misbehaves. d) SmartScreen rule can be disabled if you use VoodooShield. VoodooShield has it's own reputation checker, and on top of that, your browser may have it's own downloads reputation checker; so SmartScreen can be deemed optional, it is up to you.---------------------------------------------------------------------------------------
Advantages of Group Polilcy Firewall Rules.
If you deploy your firewall rules using Group Policy, and set the option of not to allow 'local' rules in the Profile, then you won't be affected by MS enabling rules that you don't want whenever they choose to. Group policy overrides always.
If you have made a lot of rules using Windows Advanced Firewall, then you can open it, and open Gpedit along side. Then copy the section of rules from Adv Firewall and paste it into Gpedit. Saves you a lot of work. -
Control 7: Continuous Vulnerability Management
Why is this Control critical?
Cyber defenders are constantly being challenged from attackers who are looking for vulnerabilities
within their infrastructure to exploit and gain access. Defenders must have timely threat information
available to them about: software updates, patches, security advisories, threat bulletins, etc., and
they should regularly review their environment to identify these vulnerabilities before the attackers
do. Understanding and managing vulnerabilities is a continuous activity, requiring focus of time,
attention, and resources.
Attackers have access to the same information and can often take advantage of vulnerabilities more
quickly than one can remediate. While there is a gap in time from a vulnerability being
known to when it is patched, defenders can prioritize which vulnerabilities are most impactful to the
enterprise, or likely to be exploited first due to ease of use. For example, when researchers or the
community report new vulnerabilities, vendors have to develop and deploy patches, indicators of
compromise (IOCs), and updates. Defenders need to assess the risk of the new vulnerability,
regression-test patches, and install the patch.
There is never perfection in this process. Attackers might be using an exploit to a vulnerability
that is not known within the security community. They might have developed an exploit to this
vulnerability referred to as a “zero-day” exploit. Once the vulnerability is known in the community,
the process mentioned above starts. Therefore, defenders must keep in mind that an exploit might
already exist when the vulnerability is widely socialized. Sometimes vulnerabilities might be known
within a closed community (e.g., vendor still developing a fix) for weeks, months, or years before it is
disclosed publicly. Defenders have to be aware that there might always be vulnerabilities they cannot
remediate, and therefore need to use other controls to mitigate.
People that do not assess their infrastructure for vulnerabilities and proactively address
discovered flaws face a significant likelihood of having their assets compromised.The CIS Controls have 18 security controls. Vulnerability Management is just one of them. You can download the PDF (https://learn.cisecurity.org/cis-controls-d…TEkajI3JGwwJGgw) ( It requires a business email, but you should be able to use a temporary email site ) . It has a to-do list for each of the 18 controls.
The main point is, for good security, you should not rely on just one or two controls - you need to do it holistically and cover all the bases.
The second point is that security is a process. You have to upkeep your security, like doing continuous vulnerability scans and patching.
-
Not really. Never have been a collector of movies.
-
Just watched this: Ocean 8 (Prime Video)
External Content youtu.beContent embedded from external sources will not be displayed without your consent.Through the activation of external content, you agree that personal data may be transferred to third party platforms. We have provided more information on this in our privacy policy. -
Just watched: Kung Fu Panda (Prime Videos). Some good master disciple wisdom dialog.
External Content youtu.beContent embedded from external sources will not be displayed without your consent.Through the activation of external content, you agree that personal data may be transferred to third party platforms. We have provided more information on this in our privacy policy. -
An intresting one I saw a week ago: Salmon Fishing in Yemen
External Content youtu.beContent embedded from external sources will not be displayed without your consent.Through the activation of external content, you agree that personal data may be transferred to third party platforms. We have provided more information on this in our privacy policy. -
I watch movies on my TV using a Roku device. ( TV is old and doesn't have streaming built in). So I can't use a vpn because Roku doesn't have it. I have Netflix on Roku, I used to subscribe to it. Right now I just subscribe to Amazon Prime. Plus I have the other 2 ad-supported platforms.
-
Just watched this yesterday: Constantine ( Prime video )
External Content youtu.beContent embedded from external sources will not be displayed without your consent.Through the activation of external content, you agree that personal data may be transferred to third party platforms. We have provided more information on this in our privacy policy. -
I use a few free streaming services: Tubi, Plex. And I subscribe to Amazon Prime Video. Because they all have movie trailers (the free ad-based ones sometimes don't)
-
Ubuntu Hardening Guide: