We have a new member, his name is CyberBot
If you need help, tag his name in a post and he will help you.
We have a new member, his name is CyberBot
If you need help, tag his name in a post and he will help you.

This week, Google has launched an AI Vulnerability Reward Program dedicated to security researchers who find and report flaws in the company's AI systems.
The new bug bounty program focuses on the most impactful issues in the highest-profile AI products, including but not limited to Google Search (on google.com), Gemini Apps (Web, Android, and iOS), and Google Workspace core applications (e.g., Gmail, Drive, Meet, Calendar, and others).
Other in-scope products include AI features in high-sensitivity Google AI products, such as AI Studio and Jules, as well as Google Workspace non-core apps and other AI integrations in Google products.
The rewards for vulnerabilities can reach up to $30,000 for individual quality reports with novelty bonus multipliers, while a standard security flaw report detailing security bugs that could trigger rogue actions in a flagship product comes with a top bounty of up to $20,000.
Researchers can also get a $15,000 award for sensitive data exfiltration bugs, and up to $5,000 for phishing enablement and model theft issues.
| Category / VRP Product Tier | Flagship | Standard | Other |
|---|---|---|---|
| S1: Rogue Actions | $20,000 | $15,000 | $10,000 |
| S2: Sensitive Data Exfiltration | $15,000 | $15,000 | $10,000 |
| A1: Phishing Enablement | $5,000 | $500 | credit |
| A2: Model Theft | $5,000 | $500 | credit |
| A3: Context Manipulation | $5,000 | $500 | credit |
| A4: Access Control Bypass | $2,500 | $250 | credit |
| A5: Unauthorized Product Usage | $1,000 | $100 | credit |
| A6: Cross-user Denial of Service | $500 | $100 | credit |
"In October 2023, we announced Google's reward criteria for reporting bugs in AI product, extending our Abuse Vulnerability Reward Program (VRP) to foster third-party discovery and reporting of issues and vulnerabilities specific to our AI systems," Google said.
"As we celebrate the second year of AI bug bounties at Google, we're excited to discuss what we've learned, and to announce the launch of our new, dedicated AI Vulnerability Reward Program!"
In March, the company also announced that it had awarded almost $12 million in bug bounty rewards to 660 researchers who discovered and reported security bugs through the company's Vulnerability Reward Program (VRP) in 2024.
Google has awarded $65 million in bug bounties since its first vulnerability reward program went live in 2010, with the highest reward paid last year exceeding $110,000.
One year earlier, in 2023, the search giant also paid $10 million to 632 researchers for responsibly reporting security flaws in its products and services.

Discord says they will not be paying threat actors who claim to have stolen the data of 5.5 million unique users from the company's Zendesk support system instance, including government IDs and partial payment information for some people.
The company is also pushing back on claims that 2.1 million photos of government IDs were disclosed in the breach, stating that approximately 70,000 users had their government ID photos exposed.
While the attackers claim the breach occurred through Discord's Zendesk support instance, the company has not confirmed this and only described it as involving a third-party service used for customer support.
"First, as stated in our blog post, this was not a breach of Discord, but rather a third-party service we use to support our customer service efforts," Discord told BleepingComputer in a statement.
"Second, the numbers being shared are incorrect and part of an attempt to extort a payment from Discord. Of the accounts impacted globally, we have identified approximately 70,000 users that may have had government-ID photos exposed, which our vendor used to review age-related appeals."
"Third, we will not reward those responsible for their illegal actions."
According to the threat actor, they gained access to Discord’s Zendesk instance for 58 hours beginning on September 20, 2025. However, the attackers say the breach did not stem from a vulnerability or breach of Zendesk but rather from a compromised account belonging to a support agent employed through an outsourced business process outsourcing (BPO) provider used by Discord.
As many companies have outsourced their support and IT help desks to BPOs, they have become a popular target for attackers to gain access to downstream customer environments.
The hackers allege that Discord's internal Zendesk instance gave them access to a support application, known as Zenbar, that allowed them to perform various support-related tasks, such as disabling multi-factor authentication and looking up users’ phone numbers and email addresses.
Using access to Discord's support platform, the attackers claimed to have stolen 1.6 terabytes of data, including around 1.5 TB of ticket attachments and over 100 GB of ticket transcripts.
The hackers say this consisted of roughly 8.4 million tickets affecting 5.5 million unique users, and that about 580,000 users contained some sort of payment information.
The threat actors themselves acknowledged to BleepingComputer that they are unsure how many government IDs were stolen, but they believe it is more than 70,000, as they say there were approximately 521,000 age-verification tickets.
The threat actors also shared a sample of the stolen user data, which can include a wide variety of information, including email addresses, Discord usernames and IDs, phone numbers, partial payment information, date of birth, multi-factor authentication related information, suspicious activity levels, and other internal information.
The payment information for some users was allegedly retrievable through Zendesk integrations with Discord's internal systems. These integrations reportedly allowed the attackers to perform millions of API queries to Discord's internal database via the Zendesk platform and retrieve further information.
The hacker said the group demanded $5 million in ransom, later reducing it to $3.5 million, and engaged in private negotiations with Discord between September 25 and October 2.
After Discord ceased communications and released a public statement about the incident, the attackers said they were "extremely angry" and plan to leak the data publicly if an extortion demand is not paid.

I use a few free streaming services: Tubi, Plex. And I subscribe to Amazon Prime Video. Because they all have movie trailers (the free ad-based ones sometimes don't)
Ever tried Netflix ? When using VPN you can watch Netflix from all over the world, from different countries , so a lot of content.
Ubuntu Hardening Guide:
Very useful this guide, i used it when i was still on Ubuntu.
If you are on Ubuntu, make sure to check this out !

A new variant of the FileFix social engineering attack uses cache smuggling to secretly download a malicious ZIP archive onto a victim’s system and bypassing security software.
The new phishing and social engineering attack impersonates a "Fortinet VPN Compliance Checker" and was first spotted by cybersecurity researcher P4nd3m1cb0y, who shared information about it on X.
In a new report by cybersecurity firm Expel, cybersecurity researcher Marcus Hutchins shares more details on how this attack works.
For those not familiar with FileFix attacks, they are a variant of the ClickFix social engineering attack developed by Mr.d0x. Instead of tricking users into pasting malicious commands into operating system dialogs, it uses the Windows File Explorer address bar to execute PowerShell scripts stealthily.
In the new phishing attack, a website displays a dialog that poses as a Fortinet VPN "Compliance Checker, directing users to paste what looks like a legitimate network path to a Fortinet program on a network share.
🚨 Welcome to CyberTopix! 🔐
Hey everyone! 👋
Welcome to CyberTopix — your new go-to hub for everything cybersecurity, malware analysis, and all things infosec. Whether you're a seasoned pro, a curious learner, or just starting your journey into the world of cyber, you're in the right place.
Here’s what we’re all about:
🛡️ Cybersecurity – From threat intelligence to defense strategies, we dive deep into the ever-evolving world of cyber threats and how to stay ahead of them.
🧪 Malware Testing & Analysis – Explore the dark corners of the web with us as we dissect malware, share tools, and discuss best practices for safe and effective analysis.
💬 Community First – We believe in building a positive, respectful, and inclusive space where everyone can learn, share, and grow together. No gatekeeping, no drama — just good vibes and great knowledge.
💡 The Usual & Beyond – Expect news, tutorials, tool reviews, CTF discussions, and the occasional meme to keep things fun.
So grab your virtual coffee ☕, introduce yourself, and let’s build something amazing — together.
Stay sharp. Stay safe. Stay curious.
— The CyberTopix Team
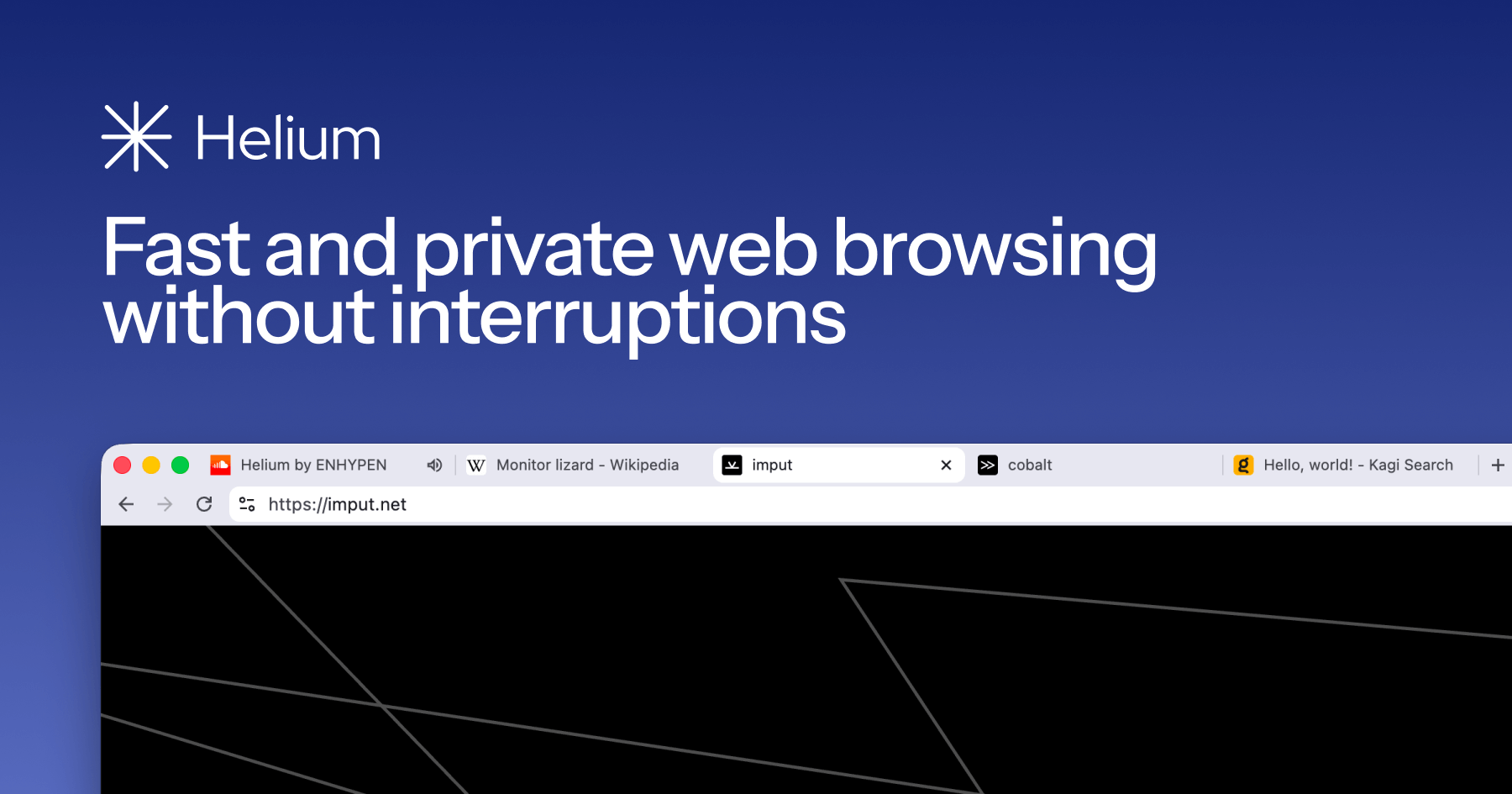
Helium blocks ads, trackers, phishing websites, and other nonsense by default, thanks to community filters and uBlock Origin.
The browser itself doesn't have any ads, trackers, or analytics. Helium also doesn't make any web requests without your explicit consent, it makes zero web requests on first launch.
All Chromium extensions are supported and work right away, by default, including all MV2 extensions.
Helium anonymizes all internal requests to the Chrome Web Store via Helium services. Thanks to this, Google can't track your extension downloads or target ads using this data. No other browser does this.
All parts of the Helium browser are open source, including online services. You can self-host Helium services and use your own instance in your browser.
Helium enforces HTTPS on all websites and warns you when a website doesn't support it. Passkeys just work.
There's no built-in password manager. Passwords should be separate from a web browser to be truly secure and immutable.
There's also no cloud-based history/data sync. You should be the only one with access to your browsing data, not some conglomerate.
We release new Chromium updates (such as security patches) as soon as possible. Your browser will always be safe and up to date.
On Windows, in-browser auto-updates are not available yet, but will become available in the future.
Since the death of John McAfee in 2021, the company he founded has undergone significant changes and developments, both in ownership and strategic direction.
McAfee has evolved from a traditional antivirus provider into a comprehensive cybersecurity platform, with a strong focus on:
Too bad the forced upselling is still in the paid versions.
I complained to Kim Allman - Board of Directors from Gen Digital about this, she will internally discuss this. ( well she said she will )
Lets hope they will get rid of the scare tactics.
Norton 360 Deluxe 25.9.10453 (build 25.9.10453.953)
Virus definitions 250930-10
UI version 1.0.104

I have Netflix and ESPN Soccer. The one i use the most is ESPN.
Telegram CEO Pavel Durov recently warned that a ‘dark, dystopian’ world is approaching fast. Sharing a post on microblogging platform X (formerly Twitter), Durov writes: “I’m turning 41, but I don’t feel like celebrating”. In the post, Durov argued that he did not feel like celebrating, arguing that “our generation is running out of time to save the free Internet built for us by our fathers.”Durov, who founded Telegram in 2013 as a privacy-focused messaging platform, said the original promise of the internet as a space for the free exchange of ideas was being replaced by tools of government control. He cited measures such as digital IDs in the UK, mandatory online age checks in Australia, and proposals for mass scanning of private messages in the European Union as signs of growing restrictions.“Germany is persecuting anyone who dares to criticize officials on the Internet. The UK is imprisoning thousands for their tweets. France is criminally investigating tech leaders who defend freedom and privacy,” Durov claimed in his post.He warned that these policies risked pushing the world toward a “dark, dystopian” future where freedoms would vanish. “Our generation risks going down in history as the last one that had freedoms — and allowed them to be taken away,” he wrote.
Durov argued that society was being misled into believing its main goal was to “destroy everything our forefathers left us: tradition, privacy, sovereignty, the free market, and free speech.” Without a course correction, he said, the result would be “self-destruction — moral, intellectual, economic, and ultimately biological.”Closing his message, Durov said he would not celebrate his birthday: “I’m running out of time. WE are running out of time.”

Disney , Netflix , HBO ?
Which one do you use and are you satisfied with it ?
v7.00.984 (06 Oct 2025)
Say hello to CCleaner 7. It’s faster, smarter, and easier to use. Enjoy a cleaner interface, dark mode options, and support for even more devices. We’ve also improved key tools like the Uninstaller and Disk Analyzer to give you more control over your PC’s performance.
Enhanced Uninstaller
Improved Disk Analyzer
Sleek new design + expanded support
Try the new CCleaner 7 now!
I am using Smart Security Premium now and i really like it, very light on the system and i like the configurations options it has.
Protection wise, and with Liveguard it shows that is very capable of catching the new threads out there.
I know it is more expensive compared to other solutions, but that is oke for me.
I keep my findings posted here.
Who is using Bitwarden and what are your thoughts ?
If you have questions or remarks you can post it here.




